"Stop using SMB1"
Option 1: Apply Patch to Host
Option 1: Apply Patch to Host
Microsoft released a patch, KB4012598, addressing this group of
vulnerabilities.
To install it, download the patch from the Microsoft Update Catalog for the corresponding host operating system.
NOTE: See here for more details.
Option 2: Disable SMBv1 via Group Policy
Option 2: Disable SMBv1 via Group Policy
To disable the SMBv1 client, the services registry key needs to be updated to disable the start of MRxSMB10 and then the dependency on MRxSMB10 needs to be removed from the entry for LanmanWorkstation so that it can start normally without requiring MRxSMB10 to first start.
This guidance updates and replaces the default values in the following two items in the registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\mrxsmb10HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanWorkstation
To configure this by using Group Policy, follow these steps:
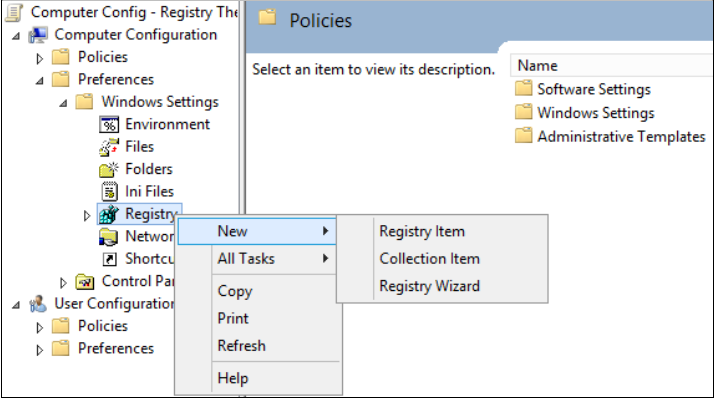
- Open the Group Policy Management Console. Right-click the GPO that should contain the new preference item, and then click Edit.
- In the console tree under Computer Configuration, expand the Preferences folder, and then expand the Windows Settings folder.
- Right-click the Registry node, point to New, and select Registry Item.
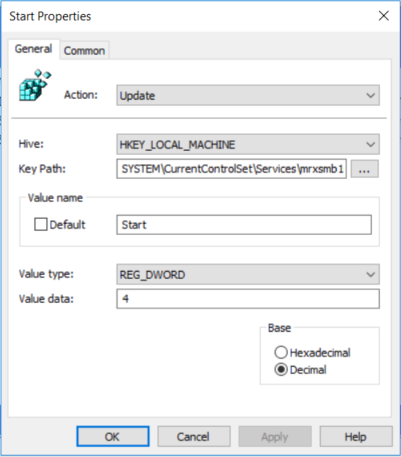
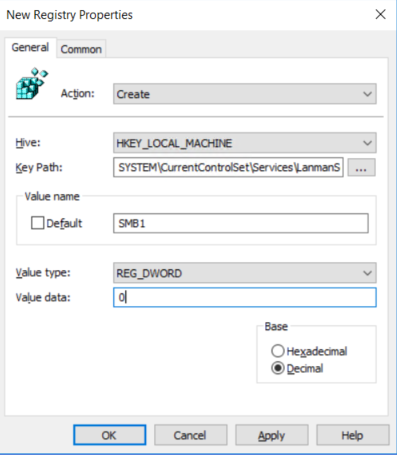
- In the New Registry Properties dialog box, select the following:
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\services\mrxsmb10
- Value name: Start
- Value type: REG_DWORD
- Value data: 4
NOTE: The default value includes MRxSMB10 in many versions of Windows, so by replacing them with this multi-value string, it is in effect removing MRxSMB10 as a dependency for LanmanServer and going from four default values down to just these three values above.
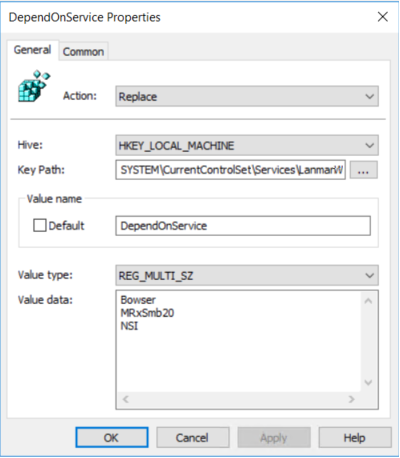
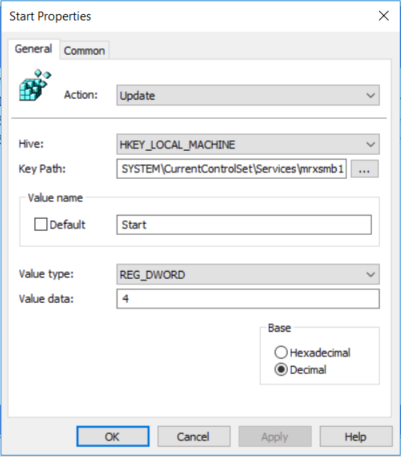
5.Then remove the dependency on the MRxSMB10 that was disabled. In the New Registry Properties dialog box, select the following:
- Action: Replace
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Services\LanmanWorkstation
- Value name: DependOnService
- Value type: REG_MULTI_SZ
- Value data:
- Bowser
- MRxSmb20
- NSI
NOTE: These three strings will not have bullets (see the following screenshot).
NOTE: When you use Group Policy Management Console, you don’t have to use quotation marks or commas. Just type each entry on individual lines.
6.Restart the targeted systems to finish disabling SMB v1.
Option 3: Disable SMBv1 Server via Group Policy
This procedure configures the following new item in the registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Configured with:
- Registry entry: SMB1
- REG_DWORD: 0 = Disabled
To use Group Policy to configure this, follow these steps:
- Open the Group Policy Management Console. Right-click the Group Policy object (GPO) that should contain the new preference item, and then click Edit.
- In the console tree under Computer Configuration, expand the Preferences folder, and then expand the Windows Settings folder.
- Right-click the Registry node, point to New, and select Registry Item
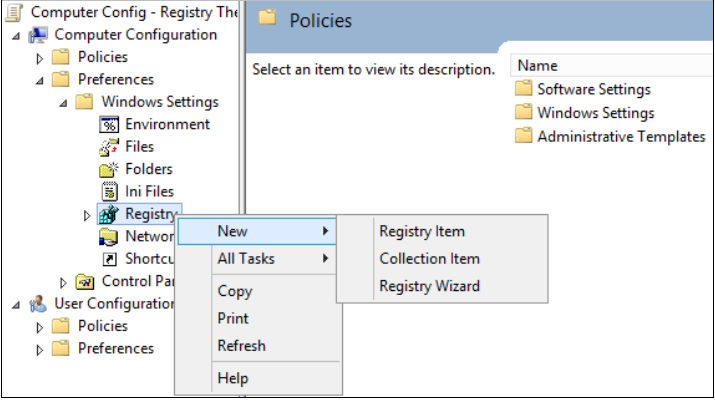
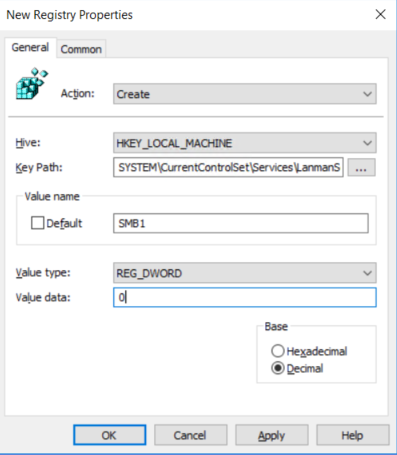
- In the New Registry Properties dialog box, select the following:
- Action: Create
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
- Value name: SMB1
- Value type: REG_DWORD
- Value data: 0
This procedure disables the SMBv1 Server components. This Group Policy must be applied to all necessary workstations, servers, and domain controllers in the domain.
Option 4: Block Access to SMB from Untrusted Hosts
Option 4: Block Access to SMB from Untrusted Hosts
Microsoft recommends restricting the use of SMB in general to hosts that do not host SMB shares. To restrict the use of SMB, follow the official Microsoft guide for disabling “Inbound connections to a computer”.
See Prevent SMB Traffic from Lateral Connections for more details.

 NOTE:
NOTE: